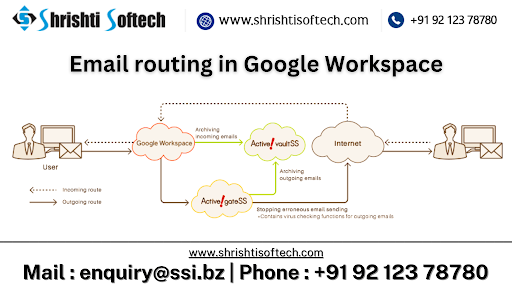
Email routing in Google Workspace allows you to control how incoming emails are handled and delivered within your organization. It provides flexibility in directing emails to specific users or groups based on various conditions and rules.
Here’s an overview of email routing options in Google Workspace :
Default Routing : This is the primary method for routing incoming emails within Google Workspace. By default, emails are routed to the user or group with a matching primary email address or alias. You can set up aliases for users or groups to receive emails sent to different addresses.
Routing Settings : You can configure specific routing settings in the Google Admin console to define how emails are handled. These settings include routing for primary and secondary domains, routing based on user types, and routing for specific organizational units (OU).
Routing Rules : You can create routing rules to control email delivery based on various criteria. Routing rules allow you to specify conditions such as sender, recipient, subject, attachment, or message size to determine where emails should be routed. For example, you can set up a rule to forward all emails from a specific domain to a particular user or group.
Content Compliance : Content compliance rules enable you to enforce policies for incoming and outgoing emails. You can define rules to scan email content for specific keywords, attachments, or patterns and take actions such as rejecting, quarantining, or modifying the emails.
Advanced Routing : Google Workspace also provides advanced routing options such as domain-level routing, where you can route emails based on the recipient’s domain, and SMTP relay service, which allows you to configure routing for non-Google Workspace servers.