Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at assessing, changing, or destroying sensitive information; extorting money from users via ransomware; or interrupting normal business processes
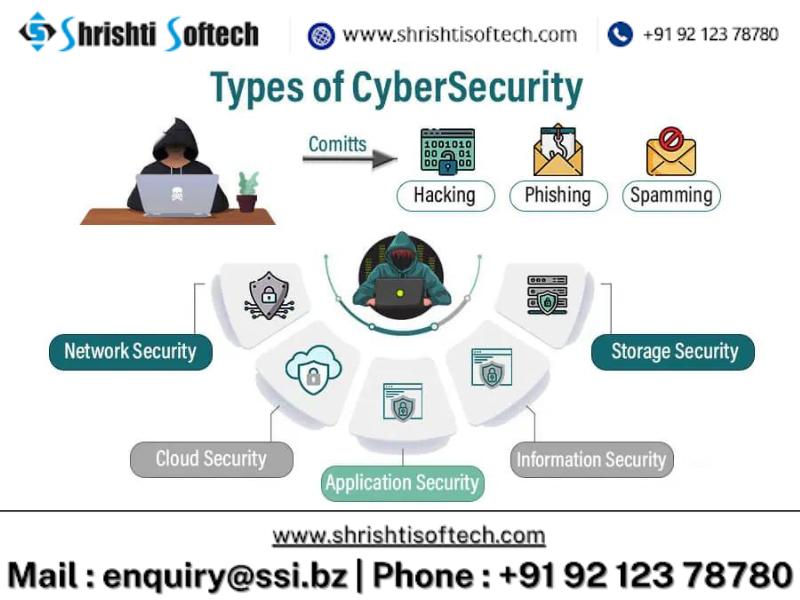
Types of cyber security :
Network Security :
Network-level safety vs. Endpoint protection : Most web security software approaches web protection from the system perspective or from the endpoint view. then network-level protection like firewalls and safe network gateways may be enough.
Application Security :
Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats such as unauthorized access and modification.
Information or Data Security :
Information privacy is concentrated on the administration of individual data— matters like putting policies in place to their own Data is being gathered, shared and utilized in appropriate ways.
Cloud Security :
While regulations force cloud engineering companies to compliance methods, it remains an on-going topic. Encryption protects when encryption key is lost, the information disappears.
Mobile Security :
Mobile information protection software offers similar features but brings increased protection for Mobile devices, communications, and authentication.
Endpoint Security :
Taken endpoint, or if it constitutes the easiest endpoint to follow faithfully, it may be applied. In particular cases, the end levels of the fatal endpoint may not require some, if any, suffering as the creature may be comatose.
Critical Infrastructure Security :
Supporting system and Critical Infrastructure protection. Critical infrastructure security is the area of concern surrounding the protection of systems, networks and assets. This plan includes further than $1.1 billion for DHS’s cybersecurity campaigns.
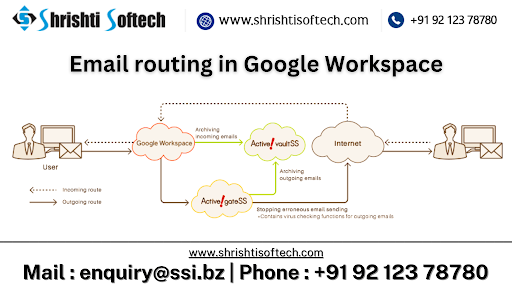
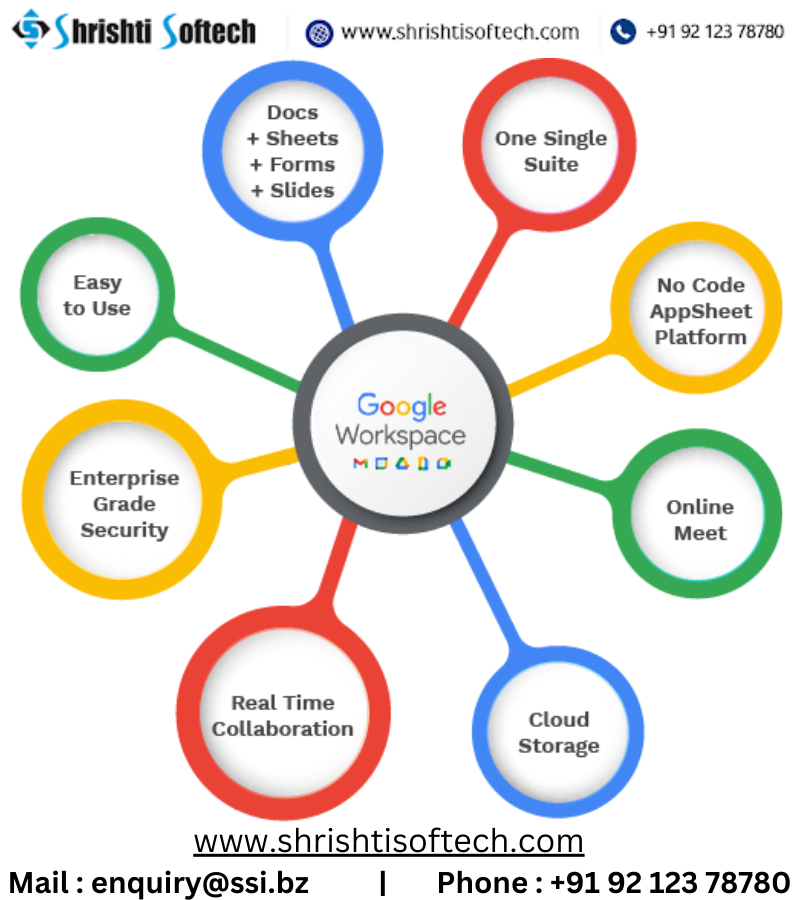
Role of cyber security in google workspace :-
Cybersecurity plays a crucial role in Google Workspace (formerly known as G Suite),
which is a suite of cloud-based productivity and collaboration tools developed by Google. As Google Workspace is widely used by individuals and organizations for communication, collaboration, and data management, ensuring the security and privacy of users’ data is of paramount importance. Here are some key aspects of the role of cybersecurity in Google Workspace:
Data Protection :
Google Workspace holds sensitive and confidential information, including emails, documents, and files. Cybersecurity measures are in place to protect this data from unauthorized access, theft, or data breaches. This includes encryption of data.
Identity and Access Management (IAM) :
Google Workspace uses robust authentication methods, such as two-factor authentication (2FA), to ensure that only authorized users can access the account. This helps prevent unauthorized access even if passwords are compromised.
Secure Communication :
Google Workspace applications, such as Gmail and Google Meet, use encryption protocols to secure communication channels and protect data from eavesdropping or man-in-the-middle attacks.
Phishing and Malware Protection :
Google deploys various security mechanisms to detect and prevent phishing attempts and malware distribution. The platform employs advanced algorithms and machine learning to identify and block suspicious activities and malicious content.
Compliance and Certifications :
Google Workspace adheres to various industry standards and certifications, such as ISO 27001, SOC 2, and GDPR, to demonstrate its commitment to security and data privacy.
User Education :
While Google ensures the security of its platform, users also play a critical role in maintaining security. Google provides resources and guidelines to educate users about best security practices, like identifying phishing attempts and safeguarding their accounts.
Overall, cybersecurity in Google Workspace is a comprehensive approach that encompasses various technological, procedural, and educational measures to safeguard user data and ensure a secure collaboration and productivity environment.